ust five years ago, most industries were concerned with simply implementing the necessary technology infrastructure for going digital. We have now arrived at an inflection point where securing those internet-connected digital assets against inevitable cyber attacks is critically important. The cyber security landscape has changed dramatically, with major distributed denial of service (DDoS)1 attacks and ransomware schemes2 routinely making headlines. According to a report by the Center for Strategic and International Studies (CSIS) and McAfee, the global cost of cybercrime was estimated at US$600 billion for 2017 — a significant jump from US$445 billion in 2014 (Lewis 2018). As more people come online and access essential services via the internet, bad actors stand to benefit a great deal from a successful attack.
The domain name system (DNS) is one of the most critical components of global internet infrastructure. When a portion of the DNS is compromised or unavailable, users cannot reach the associated resources on the internet. This is because the DNS operates as the address book for the internet and is responsible for translating Internet Protocol (IP) addresses, such as 162.219.54.2 or 2001:500:80:2::12, into human-friendly domain names, such as example.ca, and much more. Taking down elements of the DNS means entire swaths of the internet become unreachable. It is no wonder, then, that the DNS is a perennial target for cyber attackers.
Top-level domain (TLD) registry operators play an important role in ensuring the DNS — and, therefore, the internet — functions on a day-to-day basis. The TLD is the string of characters to the right of the dot in a web address, such as .ca, .com or .org. TLD registry operators are responsible for maintaining a database of all domain names for their TLD. Registry operators store information about each person or company that registers a domain name, as well as the administrative and technical information that makes their domain name reachable on the internet. This includes the IP addresses of the name servers associated with each domain name under management.
Taking down elements of the DNS means entire swaths of the internet become unreachable. It is no wonder, then, that the DNS is a perennial target for cyber attackers.
A country code TLD, or ccTLD, has two letters and is generally designated for use by a particular country, sovereign state or autonomous territory. The Canadian Internet Registration Authority (CIRA) manages the stewardship of .ca on behalf of all Canadians. In addition to country codes, there are over one thousand generic top-level domains (gTLD), from the ever-popular .com and .org, to newer generic TLD strings such as .sucks or .guru.
As security threats ramp up, it is critical that businesses vigilantly monitor and protect against security threats on two primary axes: databases and information technology (IT) infrastructure. For a TLD registry operator like CIRA, this means securing the databases associated with the domain name registry and the DNS infrastructure that supports public domain name resolution. For a bank, this translates into protecting databases containing customers’ valuable personal information and any internet-connected infrastructure that supports financial transactions. For a social media platform, this involves protecting users’ personal data and securing the infrastructure that ensures global service availability.
Data Security
Equifax and Cambridge Analytica may be household names, but for the worst of reasons. An organization’s reputation is only as good as its data security controls. Regulators are cracking down on poor information security practices, and people are acutely aware of the harm associated with personal information divulged in a data breach. Financial institutions and large corporations remain targets of data theft, but phishing schemes and attacks against small businesses, municipalities and universities are increasing.
A 2018 CIRA survey of 500 individuals with responsibility over IT security decisions found that 66 percent of businesses with 250 to 499 employees experienced a cyber attack in the last 12 months, and an estimated 70 percent of data breaches occur at companies with fewer than 100 employees (CIRA 2018). Whether it is collected for the purposes of providing a service, selling advertising or for analytics more generally, personal information retained by any organization is stored in a database. Regardless of the size or nature of a business, these databases are prime targets for cyber attackers.
Threat Vectors
For a TLD operator, the integrity of the registry is critical to its operations. Depending on its operational model, a TLD can provide internet-accessible services to its domain name distribution channel partners (registrars) and/or to individual domain name owners (registrants). In all cases, the integrity of the registry is dependent on the ability of the registrar and registrant to protect their system access credentials. Like other service providers who allow users to access systems online, many TLD operators are enforcing enhanced security mechanisms such as two-factor authentication and IP address whitelisting.
It is not uncommon for a company to notify customers of an undetected breach that occurred months or even years earlier. The primary threat CIRA encounters as a registry is compromised registrars or registrants, where a bad actor infiltrates their systems and then lies in wait before changing the attributes of domain names in order to carry out the attack of choice. This often takes the form of pointing a domain name toward a compromised site instead of the rightful registrant’s intended content. Attackers tend to target high-profile, high-traffic domain names and redirect unsuspecting users toward malicious sites that prompt them to enter personal information or that implant malware into their browser.
Also related to registry security is the prevention of phishing and malware distribution via doppelgänger domains or “typosquatting.” These attack vectors involve new domain registrations that imitate existing, usually high-traffic, domains with similar spellings or easily mistyped permutations. Doppelgänger sites are generally used for distributing malware and executing phishing schemes, usually by imitating financial institutions or government agencies to collect valuable personal information that can be used to steal identities and drain bank accounts.
Typosquatters also harvest personal information via email by registering domains that omit the dot between a company’s host name and their subdomain. When a user sends an email to [email protected] rather than [email protected], the contents of the email are shared with the typosquatter, thereby opening a phishing opportunity.
Prevention and Mitigation
To prevent attackers from accessing valuable personal information, the domain name industry has responded by implementing state-of-the-art controls to protect security management systems and lock down access, so that only authorized registrars have the ability to access systems. To prevent abuse in the registry, many TLD registries have implemented these controls.
At CIRA, for example, we actively monitor new and existing domain registrations for malicious activity. Registrants also have the option of locking their domains to prevent domain abuse by using a registry lock mechanism, where changes to the domain can only be performed by an authorized person using multifactor authentication. CIRA also investigates registrations based on information we receive from partners in the cyber security ecosystem, including the Canadian Centre for Cyber Security (CCCS) and the Canadian Cyber Threat Exchange (CCTX).
Where a registration is determined to be dubious, CIRA may audit the registration via the Registrant Information Validation process. This process is in place to ensure that a given registrant meets Canadian presence requirements as per CIRA policy, which dictates that persons who wish to register a .ca domain name or sub-domain name require a legitimate connection to Canada in at least one of 18 categories. Malicious .ca registrations frequently originate from foreign registrants who do not provide documentation to prove they meet Canadian presence requirements. When a registrant fails to demonstrate compliance with the Canadian presence requirements, the domain is suspended and then cancelled.
Trends
Both the CCCS and the CCTX were established in the last two years in order to facilitate knowledge sharing of known threats and respond to the growing threat landscape. CIRA and its registrar partners have become increasingly security savvy, implementing stringent security protocols in order to prevent bad actors from infiltrating the registry. As a result, we experience very few registry compromises, but this doesn’t mean attempts are decreasing. Bad actors consistently probe the registry. Like any system that is connected to the internet, we experience steady probing and attacks against our databases.
As in any industry, domain name holders want to know that their data is being adequately protected when they entrust a company with their personal information. A key element of the value proposition of any given TLD is trust in the reputation and ability of the registry operator to police its name space and enforce its policies for registrars and registrants.
Given the nature of .ca’s Canadian presence requirements and the processes we have implemented to protect .ca’s reputation, malicious registrations are less common in CIRA’s registry than in many other TLDs. According to Spamhaus, the most abused TLD is currently .loan, with 30,399 of its 33,328 visible domains3 under management linked to malicious spam or malware distribution. Unfortunately, TLDs that do not protect their namespaces against misuse are enabling cyber attackers to engage in malicious activity such as spam attacks and infrastructure abuse.

Infrastructure Security
DDoS attacks represent the single biggest threat to internet-connected infrastructure, including the infrastructure that supports the DNS. The objective of a denial of service attack is to exhaust the computational or bandwidth resources of the target website or digital service by overwhelming the infrastructure that supports it. With a DDoS attack, the attack traffic originates from a distributed network of compromised systems recruited to simultaneously overwhelm the target with internet traffic. DDoS attacks typically require thousands of devices working in concert. This is known as a botnet, and users are often unaware their devices are participating in a botnet attack due to malware installed on their machines.
The burgeoning Internet of Things (IoT) presents a major threat to internet infrastructure and is particularly problematic for network operators running critical infrastructure. Any internet-connected device with a processor can be recruited into a DDoS attack. Attackers target vulnerabilities in the unsecured IoT devices that have flooded the consumer market, including everything from internet-connected routers and cameras to toasters and doorbells.
Threat Vectors
A TLD’s DNS infrastructure is comprised of a network of public DNS servers, located in a number of strategic geographic locations. Many public and private networks follow a similar architecture. These servers are frequently the targets of DDoS attacks.
There are two broad types of DDoS attacks: brute force and amplification. The 2016 Mirai attack against Dyn’s managed DNS infrastructure (Dyn 2016) is an example of a brute force attack. This attack leveraged hundreds of thousands of compromised IoT devices to send traffic directly to Dyn’s DNS servers and represented the largest DDoS attack to that point in the history of the internet (Woolf 2016).
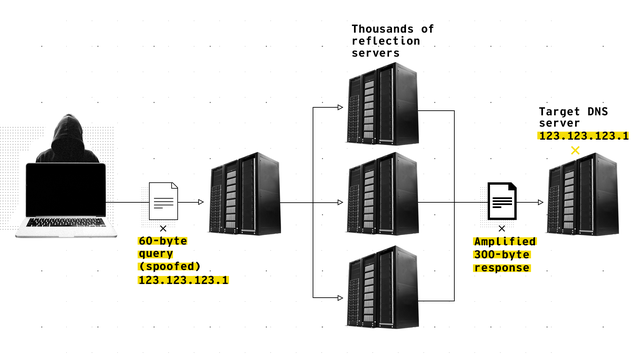
Amplification-based DDoS attacks are particularly effective against DNS infrastructure. Amplification attacks involve three elements: spoofing, reflection and then amplification. An attacker’s goal is to saturate a given server, thereby taking it offline and preventing legitimate queries from getting through. An attacker achieves this by imitating, or “spoofing,” the IP address of the target machine, then manufacturing and directing a high number of User Datagram Protocol-based queries at open public DNS, Simple Network Management Protocol and Network Time Protocol servers. Operating public DNS servers makes DNS registry operators a prime target for large-scale amplification attacks.
Thousands of open servers perceive the attack queries as originating from the target server, then reflect the attack from the source toward the attacker’s intended target. In the case of attacks that harness DNS infrastructure, the problem is compounded because a small 64-byte DNS query can be crafted to generate a large answer with thousands of bytes in response, thereby swamping the target with a high volume of junk traffic.
A further type of amplification attack involves querying thousands of open Memcached servers, which are typically used to improve the performance of database-driven web sites. Such was the case in the February 2018 amplification attack against the world’s largest software version control service, GitHub. Attackers sent several thousand queries to Memcached servers using spoofed GitHub IP addresses. The Memcached servers responded, then directed those requests to GitHub at an amplification factor of up to 51,000. The Memcached-based attack, dubbed “Memcrashed,” saturated GitHub’s infrastructure with 1.35 terabits per second of traffic, taking the service offline for 10 minutes (Kottler 2018).
Figure 1: Anatomy of a DNS DDoS Attack Showing Spoofing, Reflection and Amplification
A further threat associated with the DNS is DNS hijacking and Border Gateway Protocol (BGP) hijacking.4 This occurs when attackers wrongly and purposely announce ownership of internet resources (for example, nameservers or IP addresses) that they do not control, in effect impersonating the true managers of the resources. In a 2018 paper, researchers at the US Naval War College and Tel Aviv University described unusual patterns in BGP announcements involving China Telecom misdirecting traffic through China before delivering it to the rightful destinations in North America and Europe (Demchak and Shavitt 2018). Such attacks require extensive planning, and some are more pervasive than others.
Prevention and Mitigation
In the wake of the Mirai attack against Dyn, many stakeholders in the network operator community ramped up efforts to protect critical internet infrastructure from IoT attacks. From a TLD operator’s perspective, the current best practice to mitigate against large-scale DDoS attacks is to utilize multiple globally distributed DNS anycast providers. Local anycast nodes are not globally accessible and only serve local network peers and internet service providers (ISPs), making the nodes significantly less vulnerable to globally distributed DDoS attacks. For ccTLDs, it is a best practice to implement local anycast as close as possible to the country’s users. In Canada, CIRA operates .ca local anycast nodes connected to local internet exchange points in cities across the country.
In terms of DNS and BGP hijacking, the internet operator community has responded by developing new protocols and standards such as Domain Name System Security Extensions5 and DNS-based Authentication of Named Entities,6 which allow the rightful resource managers to sign and authenticate resources and detect traffic redirection. However, these protocols have not yet been widely adopted.
Trends
Over the last five years, attacks against the DNS have increased in frequency and intensity. This rise is directly correlated with the proliferation of botnets that are made possible by low-cost IoT consumer devices. Many of these consumer devices are visible on the public internet and have notoriously low security settings, making them easily hacked with default passwords. The aggregated bandwidth of millions of compromised “zombie” devices in a botnet has proven disastrous for the targets of attacks. Even sophisticated targets cannot sustain the brute force of upward of a terabit per second of traffic.
While the industry has responded to the problem by implementing changes to network architecture and introducing rate limits on the number of consecutive queries that a server answers, bad actors are innovating, too. Attackers are simulating traffic in ways that make sham queries appear very realistic, making it difficult to differentiate between legitimate and fraudulent traffic. Attacks also tend to generate a flurry of legitimate retry traffic as DNS servers refresh their caches in response to being prevented from completing a legitimate query. This retry activity serves to further swamp the target.
While the mischievous teenagers and organized hacktivist groups of the early Web do continue to inflict some damage, organized crime rings and state-sponsored actors are capable of much larger attacks.
The nature of attackers has also changed. While the mischievous teenagers and organized hacktivist groups of the early Web do continue to inflict some damage, organized crime rings and state-sponsored actors are capable of much larger attacks. These sophisticated actors engage in a range of malicious activity, including major DDoS campaigns, cyber espionage and election tampering. In the wake of cyber threat activity against the election processes in the United States and Europe, the newly created Canadian Security Establishment (CSE) has warned against the threat of state-controlled actors’ attempts to influence the democratic process in Canada (CSE 2018).
Hyperlocalization of infrastructure is a new trend developing in response to ever-growing DDoS attacks. For a TLD operator, the goal of hyperlocalizing infrastructure is to situate root and TLD zone files on or as close as possible to an ISP’s recursive DNS servers. Network operators are also closely monitoring new encryption protocols coming out of the Internet Engineering Task Force such as DNS over Transmission Control Protocol and DNS over Hyper Text Transfer Protocol Secure. The implementation of these new protocols is still very new, and the associated potential threats remain unknown at this time.
Conclusion
Prevention of data theft remains a high priority in the technology industry, but threats to infrastructure posed by IoT-enabled botnets are growing in frequency and severity. There is no silver bullet for mitigating the threats that cyber attacks pose to data security or critical internet infrastructure. The network operator industry and wider internet community have responded to new threats with a multi-layered approach, including everything from threat monitoring and knowledge-sharing to redesigning networks and developing entirely new protocols.
- See https://en.wikipedia.org/wiki/Denial-of-service_attack.
- See https://en.wikipedia.org/wiki/Ransomware.
- See www.spamhaus.org/statistics/tlds/.
- See https://en.wikipedia.org/wiki/BGP_hijacking.
- See https://en.wikipedia.org/wiki/Domain_Name_System_Security_Extensions.
- See https://en.wikipedia.org/wiki/DNS-based_Authentication_of_Named_Entities.
Works Cited
CIRA. 2018. “Fall 2018 Cybersecurity Survey.” October 26.
https://cira.ca/2018-cybersecurity-survey-report.
CSE. 2018. Cyber Threats to Canada’s Democratic Process. September 27.
https://cyber.gc.ca/en/guidance/cyber-threats-canadas-democratic-process.
Demchak, Chris C. and Yuval Shavitt. 2018. “China’s Maxim — Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking.” The Journal of Military Cyber Professionals Association 3 (1). https://scholarcommons.usf.edu/cgi/viewcontent.cgi?article=1050&context=mca.
Dyn. 2016. “Dyn Analysis Summary of Friday October 21 Attack.” October 26.
https://dyn.com/blog/dyn-analysis-summary-of-friday-october-21-attack/.
Kottler, Sam. 2018. “February 28th DDoS Incident Report.” GitHub, March 1.
https://githubengineering.com/ddos-incident-report/.
Lewis, James. 2018. “Economic Impact of Cybercrime — No Slowing Down.” February. CSIS and McAfee. https://csis-prod.s3.amazonaws.com/s3fs-public/publication/economic-impact-cybercrime.pdf?kab1HywrewRzH17N9wuE24soo1IdhuHdutm_source=Pressutm_campaign%3Dbb9303ae70-EMAIL_CAMPAIGN_2018_02_21utm_medium%3Demailutm_term%3D0_7623d157be-bb9303ae70-194093869.
Woolf, Nicky. 2016. “DDoS attack that disrupted internet was largest of its kind in history, experts say.” The Guardian, October 26. www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet.
The opinions expressed in this article/multimedia are those of the author(s) and do not necessarily reflect the views of CIGI or its Board of Directors.