The Danger of Critical Infrastructure Interdependency
hose of us who live in the Western world have had the tremendous privilege of being able to take functioning critical infrastructure for granted. Clean water, reliable roads, high-quality health care, dependable electricity, telephones and email are all so fundamental to modern existence that it is impossible to picture life without them. The advent of the internet has made critical infrastructure more complex, more interdependent and, therefore, more fragile. We have become complacent in our reliance on critical infrastructure, but recent developments have been a rude awakening. It is now clear that cyberwarfare can have an impact on the physical world through attacks on critical infrastructure. The often dimly understood interdependencies between critical infrastructure sectors pose a grave risk. A blow to one critical infrastructure sector could cause cascading second-order effects on other sectors, leading to a large-scale catastrophe that spirals out of control. This essay will discuss a method to assess the risks to critical infrastructure that result from interdependencies related to data flows and will examine how gaps in security can have impacts in other critical infrastructure sectors.
Cyber Attacks on Critical Infrastructure
Critical infrastructure consists of the systems that have been deemed fundamental to the functioning of a society and an economy, such as energy, transportation, telecoms, the provision of food and water, and vital health services. The disruption or destruction of critical infrastructure would have an immediate and direct impact on the economic activity, day-to-day life and safety of those affected.
The advancement of cyberweapons and hackers' tool kits now permit malicious actors to attack critical infrastructure in ways that have an immediate and frightening effect on the physical world. In 2015, Ukraine was the subject of a shocking cyber attack that managed to disable a portion of the nation’s electrical grid (Greenberg 2017). The attack, widely believed to have been carried out by Russia, intentionally caused widespread blackouts for hundreds of thousands of people. Although the attack and similar incidents directed at Ukraine in the years that followed were only temporary disruptions, they provide ample evidence of the scale of damage that cyber attacks could inflict on critical infrastructure. Hospitals had to return to using pens and paper during the attack, jeopardizing the delivery of services to those who urgently needed them (Borys 2017).
The disruption or destruction of critical infrastructure would have an immediate and direct impact on the economic activity, day-to-day life and safety of those affected.
Digital technology has made the world smaller, and critical infrastructure in Western nations is not safe from this new danger. The US government has denounced Russia for infiltrating the country’s power grid and gaining remote access to energy sector computer networks (US Department of Homeland Security 2018). In 2017, the WannaCry ransomware epidemic disabled Britain’s National Health Service for several days, leading to the cancellation of 19,000 appointments (Field 2018). In Denmark, the headquarters of Maersk, responsible for around one-fifth of the world’s shipping, was brought to a standstill by the NotPetya malware, causing transportation disruptions at port facilities worldwide (Matthews 2017). Sophisticated actors can insinuate themselves into vital control systems and remain dormant and undetected for long periods of time before the right moment to strike presents itself.
As a consequence of these events, cyber attacks on critical infrastructure have become a pre-eminent concern for national security. This year’s Worldwide Threat Assessment by the US intelligence community emphasized the ability of nation-state adversaries to launch successful cyber attacks against critical infrastructure in the United States (Coats 2019). More starkly, the report of the US National Defense Strategy Commission describes how the United States is unprepared for cyber attacks on its critical infrastructure, and how this may seriously threaten the country’s military supremacy (National Defense Strategy Commission 2018).
What makes the potential consequences of a major cyber attack on critical infrastructure difficult to predict is the interdependence between various sectors. An attack on one sector could have spillover effects on the other sectors that depend on it. The transportation sector depends on the provision of electricity by the energy sector to power trains and traffic control systems, just as the energy sector relies on the timely delivery of fuel and other inputs through the transportation sector. With respect to the threat of remote infiltration, a working group of industry experts and government officials at MIT’s Internet Policy Research Initiative warned that no one currently understands the extent to which electricity generation is coupled with other sectors, and therefore the risk of “catastrophic macroeconomic failure” in the event of a cyber attack is not adequately known (Brenner 2017, 28). Arriving at a proper comprehension of the interdependency between critical infrastructure sectors is vital in order to fully appreciate the inherent risks.

Data Interdependency Assessment
The continued functioning of critical infrastructure is highly dependent on communication, which underpins everything from the logistics of order fulfillment to the financial transfers of funds and sharing of intellectual property. As a result, addressing threats to data exchanges between critical infrastructure sectors is important to their protection. Understanding the flows of data is a useful tool for identifying hidden risks. This essay reviews a method for assessing risks driven by data-dependency relationships between different industries designated as critical infrastructure, and examines how these relationships form interdependencies within critical infrastructure sectors.
There are two basic varieties of threats to data flows: threats to availability affect whether the data can be accessed when it is needed; and threats to confidentiality and integrity concern data being disclosed or changed without the reliant party’s knowledge or approval.
Data dependency is a measure of how sensitive a critical infrastructure sector is to the availability, integrity and confidentiality of data flowing between the sectors. More specifically, “dependency” reflects the one-way data-security requirements of one critical infrastructure sector on another. “Interdependency” refers to the bidirectional system of data and information being shared between critical infrastructure sectors (Macaulay 2008).
Defining Dependency in Critical Infrastructure
The metrics and analysis presented here are drawn from earlier work, in which the survey and data collection methodology are documented (ibid.). In sum, more than 100 security and communications executives from all critical infrastructure sectors were asked detailed questions about the sensitivity of information they send and receive from all other critical infrastructure sectors, in order to quantify “inbound” versus “outbound” data dependency.
Inbound data dependency is about information and data being delivered to, and consumed by, a critical infrastructure organization. Information and data arrive in the form of voice calls, internet-based business systems and services, and even social media and other employee activities. Inbound dependency, therefore, involves the cyber security properties of information needed by critical infrastructure organizations to continue the production of goods or services. For instance, how long can a water treatment plant continue to operate safely without information from testing laboratories in the health sector? Inbound data dependency is related to the vulnerabilities of a sector that are caused by interdependency.
Outbound data dependency is about information from a given critical infrastructure sector that is sent to other critical infrastructure sectors. Websites are information assets established in part to address outbound data on a self-serve basis. Outbound dependency concerns the security requirements that other, consuming critical infrastructure sectors place on the suppliers of information. To return to the example of the water treatment plant, outbound dependency is concerned with how long the health sector can safely operate without information from the water treatment plant. Outbound dependency concerns the threat that a given critical infrastructure can pose to other critical infrastructure sectors due to interdependency.
Dependency Matrices
A dependency matrix is a means of visualizing the cyber risks associated with critical infrastructure interdependency. The dependency matrix reveals the potential vulnerability of a given critical infrastructure to threats from other critical infrastructure sectors. Table 1 is an example of a dependency matrix. Both inbound and outbound dependencies are presented through this single tool. Together, inbound and outbound dependence equal “interdependence.”
Table 1: Dependency Matrix for the 10 Critical Infrastructure Sectors
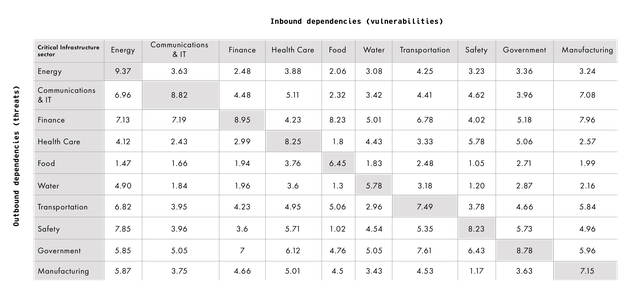
The columns for each critical infrastructure sector represent how a sector self-rates (according to interviews conducted with stakeholders) (ibid.) its dependency on information coming from other critical infrastructure sectors — the inbound dependency. Most organizations will intuitively understand their vulnerabilities regarding the information they consume. The rows represent how dependent information-receiving critical infrastructure sectors are on information and data from a given critical infrastructure sector, according to their own assessments — the outbound dependency for each sector. Unlike inbound dependency, most organizations do not have a great deal of insight into how all other critical infrastructure sectors actually need the information and data they produce.
In total, more than 4,000 distinct data dependency metrics were gathered from critical infrastructure stakeholders; dependency was ranked on a scale from 1 to 10. The higher the number in the column, the greater the dependency (vulnerability) on data flowing into a sector; the higher the number in a row, the greater the dependency (threat) of others on data flowing out of the sector. By mapping out critical infrastructure interdependencies in this way, we can begin to understand — and take precautions against — the sort of cascading effects that might follow a major cyber attack on a critical infrastructure sector.
Sector-specific Dependency Analysis: Energy Sector
The energy sector is primarily concerned with electric power generation and transmission, as well as oil and gas production and storage. Energy is often considered a “super critical” infrastructure because most other critical infrastructure sectors cannot operate if energy is not functioning. The following tornado diagram (Figure 1) is used to illustrate the energy sector’s inbound and outbound data dependencies and the resulting cyber vulnerabilities and threats. The diagram is divided vertically by an axis that is valued at zero. The left side displays the median inbound data dependency values for the energy sector, in descending order from highest to lowest. The right side displays the outbound data dependency values for each of the sectors (that is, how do other critical infrastructure sectors depend on the data from the energy sector?).
Figure 1: Energy Sector Data Dependency
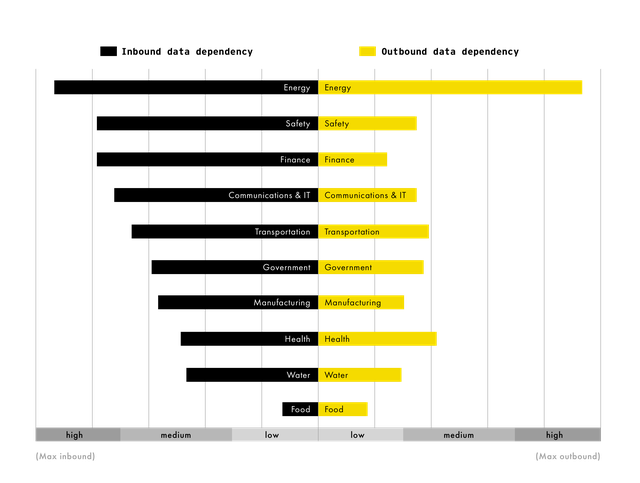
Intra-sector data dependencies are typically strongest among critical infrastructure sectors. Energy is the largest consumer of its own information and data as a result of the tight supply chain linkages between different organizations, for instance, in production versus distribution of both electricity and fossil energies.
As shown on the left side of the diagram, the energy sector is a large consumer of data from other sectors and expresses the highest overall inbound dependency and, therefore, cyber vulnerability to critical infrastructure interdependency. Energy’s inbound data and cyber requirements are heightened relative to other sectors by the high standards around energy supplies mandated by clients and government. Loss of data flows from within the energy sector itself is a serious vulnerability that might be exploited by a variety of different threats, such as unauthorized access to control systems, or an impact on energy generation when critical data flows required for plant operation are rendered unavailable.
Information and data from the safety sector (which includes law enforcement and first responders) is the second-highest inbound dependency for energy. The inability to receive security reports would significantly impair the energy sector’s ability to prepare and respond to incidents that might impact operations. This may also suggest that unauthenticated or spoofed data purporting to be from the safety sector could represent a potential pathway for cyber attacks.
Canadian and US energy grids are intertwined, such that a cyber attack that disables electricity supply in the United States could have second-order effects for Canadian critical infrastructure.
Every sector except for the energy sector itself consistently rates the information and data from the energy sector (outbound information) as a lower priority than the energy sector rates the reciprocal information (inbound information). Note that this does not indicate that other sectors think of the supply of energy itself as a low priority. Rather, energy supplies are somewhat taken for granted, with backup generators able to cover the brief power outages other sectors are accustomed to. They are likely unprepared to deal with the sort of extended outages a major cyber attack could potentially cause. This creates a vulnerability in other sectors that place a reduced emphasis on the data from the energy sector, as well as an opportunity to compromise data flows at critical times. A low outbound score also represents a threat to the energy sector itself: it may be overestimating other sectors’ responsiveness and collaboration in the event of a crisis.
Conclusions and Policy Considerations
It is obvious that cyber attacks on critical infrastructure are capable of inflicting real-world damage. The frequency and severity of such incidents will likely only increase. Western countries are beginning to formulate strategies and policy responses to meet this challenge. The United States has moved toward a more aggressive posture to defend its critical infrastructure systems against cyber attacks. The most recent Department of Defense Cyber Strategy outlines a “defend forward” policy for addressing cyber threats to US critical infrastructure, possibly including pre-emptive action (Department of Defense 2018). The US government’s most recent cyber strategy details a growing emphasis on offensive cyber operations by certain branches of the US government, and the United States has not ruled out responding to major cyber attacks on critical infrastructure through conventional forces (President of the United States of America 2018). Other governments have been more muted regarding threats of retaliation; however, all are taking seriously the cyber threat toward critical infrastructure.
Governments have an urgent need to achieve a clearer understanding of the often-opaque interdependencies between critical infrastructure sectors, and to take steps to mitigate the chances of cascading chain reactions. Industry experts have suggested that government could have a role to play in coordinating stress test exercises and simulations between critical infrastructure sectors, which could illuminate present weaknesses and build resilience (Brenner 2017).
Works Cited
Borys, Christian. 2017. “The day a mysterious cyber-attack crippled Ukraine.” BBC, July 4. www.bbc.com/future/story/20170704-the-day-a-mysterious-cyber-attack-crippled-ukraine.
Brenner, Joel. 2017. Keeping America Safe: Toward More Secure Networks for Critical Sectors. MIT Center for International Studies. https://internetpolicy.mit.edu/reports/Report-IPRI-CIS-CriticalInfrastructure-2017-Brenner.pdf.
Coats, Daniel. 2019. Worldwide Threat Assessment of the US Intelligence Committee. January 29. www.dni.gov/files/ODNI/documents/2019-ATA-SFR---SSCI.pdf.
Department of Defense. 2018. Department of Defense Cyber Strategy Summary. https://media.defense.gov/2018/Sep/18/2002041658/-1/-1/1/CYBER_STRATEGY_SUMMARY_FINAL.PDF.
Field, Matthew. 2018. “WannaCry cyber attack cost the NHS £92m as 19,000 appointments cancelled.” The Telegraph, October 11. www.telegraph.co.uk/technology/2018/10/11/wannacry-cyber-attack-cost-nhs-92m-19000-appointments-cancelled/.
Greenberg, Andy. 2017. “How an Entire Nation Became Russia’s Test Lab for Cyberwar.” Wired, June 20. www.wired.com/story/russian-hackers-attack-ukraine/.
Macaulay, Tyson. 2008. Critical Infrastructure: Understanding Its Component Parts, Vulnerabilities, Operating Risks, and Interdependencies. Boca Raton, FL: CRC Press.
Matthews, Lee. 2017. “NotPetya Ransomware Attack Cost Shipping Giant Maersk Over $200 Million.” Forbes, August 16. www.forbes.com/sites/leemathews/2017/08/16/notpetya-ransomware-attack-cost-shipping-giant-maersk-over-200-million/#5cbb07084f9a.
National Defense Strategy Commission. 2018. Providing for the Common Defense: The Assessment and Recommendations of the National Defense Strategy Commission. www.usip.org/sites/default/files/2018-11/providing-for-the-common-defense.pdf.
President of the United States of America. 2018. National Cyber Strategy of the United States of America. www.whitehouse.gov/wp-content/uploads/2018/09/National-Cyber-Strategy.pdf.
US Department of Homeland Security. 2018. “Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors.” Alert (TA18-074A). www.us-cert.gov/ncas/alerts/TA18-074A.
The opinions expressed in this article/multimedia are those of the author(s) and do not necessarily reflect the views of CIGI or its Board of Directors.